While servers require more involvement and active maintenance, some aspects of the installation process are, in fact, streamlined, i.e. a server distro is designed to take over an entire hard disk which eradicates the need to define partitions. The firewall distros in this roundup go to great lengths to help you mould the installation as per your network configuration. All of them use browser-based interfaces that can be used to monitor and modify the various components of the firewall.
Having a graphical interface is crucial as a technologically sound base isn’t enough by itself, since a convoluted or illogically arranged management interface will have a direct bearing on a distro’s usability and prevent users from getting the most out of it.
We’ll break this slide down into mini-reviews of the deployment experience, starting with…
IPFire
IPFire is written from scratch and has a straightforward installation process. The installer will detect the number of NICs attached to the computer and ask you to assign them to one of the four colour-coded zones. Each of these zones caters to a group of machines that share a common security level. Later on you’ll be asked to assign an IP address to the NIC that’s connected to your internal network and will dole out IP address via DHCP.
Once you’ve installed the distro, fire up its browser-based admin interface which is available on the IP address you assigned to the NIC connected to the local network. Head to the Firewall section in the admin interface to define the rules for the firewall. While the interface is simple to use, it requires some expertise for effective deployment and some time spent with IPFire’s documentation.
Score: 3/5
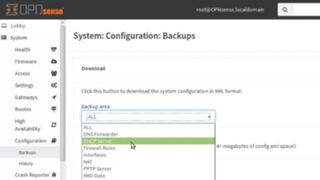
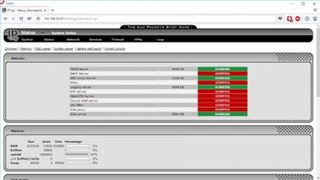
OPNsense
This distro was forked from pfSense and follows the same straightforward installation procedure. After installation, the distro boots to the command-line dashboard which also includes the address of the browser-based admin console. The admin interface is the one major visible difference between the distro and its progenitor. The interface takes you through a brief set up wizard prompting you for information about your network.
Once it’s rebooted with the right settings, head to the Rules section under Firewall. The rules definition interface is presented logically and includes a switch to display relevant help information to explain the various settings. Similarly, configuring the other components of the firewall distro is also a relatively intuitive process. Since the distro has a vast number of settings, you can enter keywords in the search box at the top of the interface to locate the relevant setting.
Score: 4/5
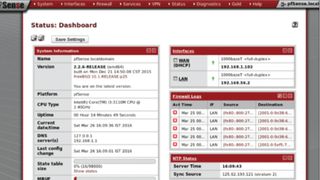
pfSense
The FreeBSD-based distros, pfSense and OPNsense, use the same fairly automated installers, though the original pfSense version offers more advanced options, including the ability to install a custom kernel. Again, just like OPNsense, pfSense boots to a console-based interface that gives you the option to configure the network interfaces on the installed machine.
Once they are all set up and configured, a browser-based console takes the user through a set up wizard. The interface isn’t the most pleasing to look at, i.e. the page for adding a new firewall rule is verbose and only contains links for relevant documentation, which are designed to help new users. The distro requires you to put some time into learning it, especially if you’re going to use the add-on packages, but the documentation is worth its weight in gold (if printed out).
Score: 3/5
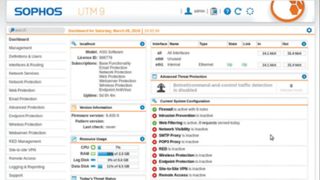
Sophos UTM
Originally known as the Astaro Security Gateway, you have to download the ISO for Sophos UTM, register on the project’s website and get a user licence which you’ll have to upload to the server when configuring it. During installation, Sophos asks you to select the NIC connected to the internal network and assign it an IP address, which you can use to access the distro’s browser-based admin interface. Users are also asked to permit installation of some proprietary components which has to be agreed to in order to use the distro.
Once installed, users are expected to bring up a browser-based management interface and run through the brief setup during which they will be asked to upload their licence. Sophos then locks down all traffic and enables you to poke holes for the type of traffic you wish to allow during the initial setup.
Score: 5/5
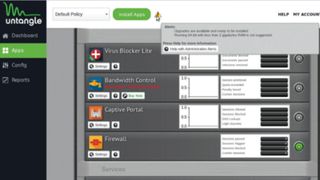
Untangle NG Firewall
The Debian-based distro is very easy to set up and is the only distro in this roundup which restarts after install into a web-based setup wizard. You’re asked to set the password for the admin user, then point to and configure the two networks cards – one that connects to the internet and the other the local network.
When setup is complete, Untangle prompts you to create a free account in order to configure the server. You’ll then have to install applications, such as the firewall, to infuse that functionality into the server. Almost all the applications are preconfigured and run automatically after install. You can also configure each application by clicking the ‘Settings’ button under it. Untangle’s dashboard also enables you to analyse the traffic passing through the server, and each application will show statistics for its own traffic as well.
Score: 4/5